KNEC Computer Studies Paper 1 Question Paper / 2016 KCSE MOKASA Joint Examination
2016 KCSE MOKASA Joint Examination
Computer Studies Paper 1
SECTION A (40 Marks)
ANSWER ALL QUESTIONS IN THIS SECTION
Differentiate between cold booting and warm bootingin computing
………………………………………………………………………………………………………………………………………………………………
………………………………………………………………………………………………………………………………………………………………
………………………………………………………………………………………………………………………………………………………………
………………………………………………………………………………………………………………………………………………………………
2 marks
Define parallel processing
………………………………………………………………………………………………………………………………………………………………
………………………………………………………………………………………………………………………………………………………………
1 marks
(a) Mention any TWO reasons why command-based operating systems are not common in today’s business computer systems. (2mks)
………………………………………………………………………………………………………………………………………………………………
………………………………………………………………………………………………………………………………………………………………
………………………………………………………………………………………………………………………………………………………………
………………………………………………………………………………………………………………………………………………………………
(b) Explain any THREE functions of an operating system with respect to memorymanagement
(3mks)
………………………………………………………………………………………………………………………………………………………………
………………………………………………………………………………………………………………………………………………………………
………………………………………………………………………………………………………………………………………………………………
………………………………………………………………………………………………………………………………………………………………
………………………………………………………………………………………………………………………………………………………………
5 marks
Differentiate between partitioning and formatting as used in disk management
………………………………………………………………………………………………………………………………………………………………
………………………………………………………………………………………………………………………………………………………………
………………………………………………………………………………………………………………………………………………………………
………………………………………………………………………………………………………………………………………………………………
2 marks
Name the type of scanner used to capture data from the following document format below
………………………………………………………………………………………………………………………
………………………………………………………………………………………………………………………
1 marks
Computer output can now be in form of spoken words in digitized speech. An example of such application is spell learning devices for children. State ONEadvantage of speech output.
………………………………………………………………………………………………………………………………………………………………
………………………………………………………………………………………………………………………………………………………………
1 marks
Mention any TWO features that are considered before buying a main memory module.
…………………………………………………………………………………………………………………………………………………………………
…………………………………………………………………………………………………………………………………………………………………
…………………………………………………………………………………………………………………………………………………………………
2 marks
A technician recommended a computer in the principal’s office needs upgrading of the CPU. State any TWO reasons that may have necessitated the upgrading of the CPU.
…………………………………………………………………………………………………………………………………………………………………
…………………………………………………………………………………………………………………………………………………………………
…………………………………………………………………………………………………………………………………………………………………
…………………………………………………………………………………………………………………………………………………………………
2 marks
StateTWO reasons why secondary storage is preferred to main memory in data storage.
…………………………………………………………………………………………………………………………………………………………………
…………………………………………………………………………………………………………………………………………………………………
…………………………………………………………………………………………………………………………………………………………………
…………………………………………………………………………………………………………………………………………………………………
2 marks
(a) State ONE advantage of relational database model over flat files (1mk)
…………………………………………………………………………………………………………………………………………………………………
…………………………………………………………………………………………………………………………………………………………………
…………………………………………………………………………………………………………………………………………………………………
(b) State TWO uses of primary keys in a database (2mks)
…………………………………………………………………………………………………………………………………………………………………
…………………………………………………………………………………………………………………………………………………………………
…………………………………………………………………………………………………………………………………………………………………
(c) A database requires data to be defined by assigning data types to fields for purposes of consistent storage.
Describeany FOUR data types that can be allowed in MsAccess. (4mks)
…………………………………………………………………………………………………………………………………………………………………
…………………………………………………………………………………………………………………………………………………………………
…………………………………………………………………………………………………………………………………………………………………
…………………………………………………………………………………………………………………………………………………………………
…………………………………………………………………………………………………………………………………………………………………
(d) Definethe term macro as used in databases (1mk)
…………………………………………………………………………………………………………………………………………………………………
…………………………………………………………………………………………………………………………………………………………………
8 marks
State any ONE reason why USB interface cables are widely used in computing devices
………………………………………………………………………………………………………………………
………………………………………………………………………………………………………………………
1 marks
A company is considering replacing some of its software, including its word processing package, and to acquire an integrated software package. State TWO advantages for the company in usingintegrated software rather than separate packages.
………………………………………………………………………………………………………………………
………………………………………………………………………………………………………………………
………………………………………………………………………………………………………………………
………………………………………………………………………………………………………………………
2 marks
(a) State TWO types of DTP software (2mks)
………………………………………………………………………………………………………………………
………………………………………………………………………………………………………………………
………………………………………………………………………………………………………………………
(b) List FOUR page formatting features in DTP (2mks)
………………………………………………………………………………………………………………………
………………………………………………………………………………………………………………………
………………………………………………………………………………………………………………………
4 marks
(a) Explain the meaning of “what if analysis” in spreadsheets (2mks)
………………………………………………………………………………………………………………………
………………………………………………………………………………………………………………………
………………………………………………………………………………………………………………………
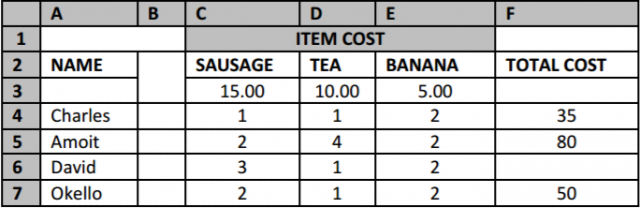
(b) The table below shows items consumed by some students for breakfast in a given day.
(i) Using anexpression,find the total expenditure incurred by David (2mks)
………………………………………………………………………………………………………………………
………………………………………………………………………………………………………………………
(ii) State what you would obtain from the expression = CountIF (F4:F7, “>45”) (1mk)
………………………………………………………………………………………………………………………
………………………………………………………………………………………………………………………
5 marks
Define the following terms as used in relation to operating systems
(i) Folder
………………………………………………………………………………………………………………………
………………………………………………………………………………………………………………………
(ii) Drive
………………………………………………………………………………………………………………………
………………………………………………………………………………………………………………………
2 marks
SECTION B (60 Marks)
ANSWER QUESTION 16 AND ANY OTHER THREE QUESTIONS FROM THIS SECTION
(a) State any THREE advantages of using Object Oriented programming for writing programs (3mks)
………………………………………………………………………………………………………………………
………………………………………………………………………………………………………………………
………………………………………………………………………………………………………………………
………………………………………………………………………………………………………………………
(b) In a computer contest with 40 entries, three papers are tested and the final marks awarded
according to the average of the papers. The final marks are then ranked to get position 1, 2 and 3
who are awarded trophy, cash and scholarship, trophy and cash, and cash respectively
Write a program pseudocode and flowchart that will prompt for the name, school and marks for
each paper then compute the final marks and rank and display the students name, school, final
marks position and award.
i. Pseudocode (5mks)
ii. Flowchart (7mks)
12 marks
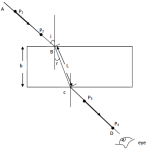
(a) With the aid of a well labeled diagram, describe control and feedback model in a system (4mks)
………………………………………………………………………………………………………………………
………………………………………………………………………………………………………………………
………………………………………………………………………………………………………………………
………………………………………………………………………………………………………………………
………………………………………………………………………………………………………………………
………………………………………………………………………………………………………………………
………………………………………………………………………………………………………………………
………………………………………………………………………………………………………………………
(b) Distinguish between the following terms as used in system development (4mks)
i. Hard system and soft system
…………………………………………………………………………………………………………………………
…………………………………………………………………………………………………………………………
…………………………………………………………………………………………………………………………
…………………………………………………………………………………………………………………………
ii. Operational feasibility and technical feasibility
…………………………………………………………………………………………………………………………
…………………………………………………………………………………………………………………………
…………………………………………………………………………………………………………………………
…………………………………………………………………………………………………………………………
(c) State THREE ways in which organizations manage system entropy (3mks)
…………………………………………………………………………………………………………………………
…………………………………………………………………………………………………………………………
…………………………………………………………………………………………………………………………
…………………………………………………………………………………………………………………………
…………………………………………………………………………………………………………………………
(d) Explain any TWO reasons for system maintenance (1mk)
…………………………………………………………………………………………………………………………
…………………………………………………………………………………………………………………………
…………………………………………………………………………………………………………………………
…………………………………………………………………………………………………………………………
(e) Briefly explain THREE ways in which computers can be used in motor vehicle manufacturing
companies (3mks)
…………………………………………………………………………………………………………………………
…………………………………………………………………………………………………………………………
…………………………………………………………………………………………………………………………
…………………………………………………………………………………………………………………………
…………………………………………………………………………………………………………………………
…………………………………………………………………………………………………………………………
15 marks
(a) Distinguish between the following terms as used in data communication (4mks)
i. Guided transmission and unguided transmission
…………………………………………………………………………………………………………………………
…………………………………………………………………………………………………………………………
…………………………………………………………………………………………………………………………
…………………………………………………………………………………………………………………………
ii. Multiplexing and demultiplexing
…………………………………………………………………………………………………………………………
…………………………………………………………………………………………………………………………
…………………………………………………………………………………………………………………………
…………………………………………………………………………………………………………………………
(b) Below is a diagram of a network topology.
i. Name the above topology (1mk)
…………………………………………………………………………………………………………………………
ii. State ONE advantages and ONEdisadvantage of using the topology named above (2mks)
…………………………………………………………………………………………………………………………
…………………………………………………………………………………………………………………………
…………………………………………………………………………………………………………………………
(c) (i) State TWO ways in which users in an organization can be a security threat to data in an
information system. (2mks)
………………………………………………………………………………….……………………………
…………………………………………………………………………………………………………………………
…………………………………………………………………………………………………………………………
…………………………………………………………………………………………………………………………
(ii)Define cyber terrorism (1mk)
…………………………………………………………………………………………………………………………
…………………………………………………………………………………………………………………………
(d) A school intends to set-up an e-mail. List FOURactivities likely to be provided by the e-mail
facility. (2mks)
…………………………………………………………………………………………………………………………
…………………………………………………………………………………………………………………………
…………………………………………………………………………………………………………………………
…………………………………………………………………………………………………………………………
(e)Define the following terms as used in the internet. (2mks)
(i)Internet blog
…………………………………………………………………………………………………………………………
…………………………………………………………………………………………………………………………
(ii) Webportals
…………………………………………………………………………………………………………………………
…………………………………………………………………………………………………………………………
(f) Kenya publishing and printing company wishes to employ an ICT professional to assist in making
publications .State the suitable ICT professional the firm could employ (1mk)
…………………………………………………………………………………………………………………………
15 marks
(a) (i)List and explain the THREE types of errors that can occur during data collection stage of data
processing cycle (3mks)
…………………………………….…………………………………………………………………………
…………………………………………………………………………………………………………………………
…………………………………………………………………………………………………………………………
…………………………………………………………………………………………………………………………
…………………………………………………………………………………………………………………………
…………………………………………………………………………………………………………………………
…………………………………………………………………………………………………………………………
(ii)Distinguish between master file and transaction file (2mks)
…………………………………….…………………………………………………………………………
…………………………………………………………………………………………………………………………
…………………………………………………………………………………………………………………………
…………………………………………………………………………………………………………………………
(iii) Define real time processing (1mk)
…………………………………………………………………………………………………………………………
…………………………………………………………………………………………………………………………
(iv) Explain a situation where the batch processing would be appropriate (1mk)
…………………………………………………………………………………………………………………………
…………………………………………………………………………………………………………………………
(b) Using twos complement, perform the following operation and give your answer in decimal
notation
• 7778 – 2510(4mks)
…………………………………………………………………………………………………………………………
…………………………………………………………………………………………………………………………
…………………………………………………………………………………………………………………………
…………………………………………………………………………………………………………………………
(c) Solve AC16+1012=X2 (2mks)
…………………………………………………………………………………………………………………………
…………………………………………………………………………………………………………………………
…………………………………………………………………………………………………………………………
…………………………………………………………………………………………………………………………
…………………………………………………………………………………………………………………………
…………………………………………………………………………………………………………………………
…………………………………………………………………………………………………………………………
…………………………………………………………………………………………………………………………
…………………………………………………………………………………………………………………………
…………………………………………………………………………………………………………………………
(d) Convert binary number 11010110.10012 into octal number. (2mks)
…………………………………………………………………………………………………………………………
…………………………………………………………………………………………………………………………
…………………………………………………………………………………………………………………………
…………………………………………………………………………………………………………………………
…………………………………………………………………………………………………………………………
…………………………………………………………………………………………………………………………
…………………………………………………………………………………………………………………………
15 marks
(a) State any TWO negative effects of introducing robots in a manufacturing plant (2mks)
…………………………………………………………………………………………………………………………
…………………………………………………………………………………………………………………………
…………………………………………………………………………………………………………………………
…………………………………………………………………………………………………………………………
(b) State THREE advantages of using computers (3mks)
…………………………………………………………………………………………………………………………
…………………………………………………………………………………………………………………………
…………………………………………………………………………………………………………………………
…………………………………………………………………………………………………………………………
…………………………………………………………………………………………………………………………
………………………………………………………………………………………………………………………
(c) Name THREE types of special purpose memories used in a computer (3mks)
…………………………………………………………………………………………………………………………
…………………………………………………………………………………………………………………………
…………………………………………………………………………………………………………………………
(d)Explain the purpose of the system clock (2mks)
…………………………………………………………………………………………………………………………
…………………………………………………………………………………………………………………………
(e) (i) In word processing, differentiate between text wrap and word wrap (2mks)
…………………………………………………………………………………………………………………………
…………………………………………………………………………………………………………………………
…………………………………………………………………………………………………………………………
…………………………………………………………………………………………………………………………
(ii) List any THREE types of section breaks used in word. (3mks)
…………………………………………………………………………………………………………………………
…………………………………………………………………………………………………………………………
…………………………………………………………………………………………………………………………
…………………………………………………………………………………………………………………………
15 marks